
The Missing Layer in OpenClaw Architectures
Liam Quinn
Estimated read time: 7 min
Last updated: February 20, 2026
How one startup runs OpenClaw in production without ever putting an API key in a config file.
OpenClaw has become the fastest-growing open source project in AI. Over 150,000 GitHub stars, a passionate community of builders, and a genuinely impressive local-first architecture that lets you run a personal AI agent on your own machine. But there's a tension at the heart of every serious OpenClaw deployment: the moment your agent needs to talk to an API, your credentials end up sitting in the same environment that processes untrusted input from the outside world. That's the problem this post is about, and how one team solved it using Jentic.
Matthew McCann, CEO and founder of PayKali, told us something a few weeks ago that stuck with me. His team had built agents across sales, software, and data science on OpenClaw, and they were working. Really working. Agents booking meetings from voice notes, pulling context from CRM records, preparing agendas from email threads.
The AI Operating System they'd been building wasn't a prototype anymore. It was running their business. And that's when the problem got real. Because the more capable their agents became, the more external services they needed to reach, and the more credentials were sitting exposed on the same machine that processed untrusted input from the outside world.
PayKali builds at the intersection of AI, supply chain, and sales, and trust is central to how they operate. Running production agents with plaintext API keys on a machine that ingests arbitrary inputs wasn't going to cut it.
So they split the architecture in two. OpenClaw kept doing what it's great at: local orchestration, agent memory, multi-step task coordination, conversational interface. And they moved every external integration behind Jentic.
The Problem
When you first get OpenClaw running, the experience is magical. You message your agent, it reads your calendar, drafts a reply, updates a board. You feel like you're living in the future.
What you don't feel, at least not immediately, is the risk you just created.
Your API keys for Google, your CRM, your email provider, your cloud storage... they're all sitting in local configuration files on the same machine your agent runs on. The same machine that processes every message, email, and web page your agent touches. There's no boundary between the thing that decides what to do and the thing that holds the keys to do it.
The security community has been loud about this. Cisco tested a third-party OpenClaw skill and found it was silently exfiltrating data to an external server. The skill had been boosted to rank number one in the repository. SecurityScorecard found over 135,000 internet-exposed instances, many leaking credentials. Researchers demonstrated a one-click RCE exploit that could hijack an instance in milliseconds.
These aren't theoretical risks. They're documented, reproducible, and in some cases actively exploited. But the deeper issue isn't any single vulnerability. It's that OpenClaw collapses orchestration and execution into one trust boundary. If anything goes wrong, and in a sufficiently complex agent setup something eventually will, the blast radius is everything your agent can touch: your email account, your CRM, your Google Workspace, your cloud storage, your calendar. One compromised instance, and an attacker has the keys to all of it.
Most OpenClaw builders I talk to are aware of this on some level. They just don't have a clean answer beyond "be careful." That's not a security model. That's hope.
What PayKali Actually Did
McCann's team uses Jentic as the integration and tooling layer for all their OpenClaw agents. The core rule is simple: OpenClaw never directly holds credentials for or connects to external services.
Here's what that looks like in practice. Their sales agents work across CRM systems, email and social messaging, and cloud storage including business plans, strategy docs, and kanban boards. When an agent needs to look up a contact in the CRM or send a calendar invite, it doesn't make a raw API call with locally stored credentials. It requests the capability through Jentic, which handles authentication, executes the call in its own managed environment, and returns the result.
"MCP is the USB of AI, and Jentic is the standardized interface that makes it safe to actually plug things in."
— Matthew McCann, CEO & Founder, PayKali
I like that framing. USB didn't just give you a port. It gave you a protocol, power management, and device isolation. The port alone isn't the point.
It's worth noting that OpenClaw founder Peter Steinberger himself has been vocal about not building native MCP support into the agent. In his recent Y Combinator interview, he said he "totally skipped the MCP crap" and prefers letting agents use CLIs directly, calling it more flexible and scalable. Fair enough. Jentic works either way. McCann's team connects through MCP where it makes sense, but if you'd rather skip MCP entirely, you can generate a Jentic API key and provide it directly to OpenClaw. Your agent calls Jentic through the CLI, Jentic handles credentials and execution on the other side, and you get all the same security benefits. The integration path is flexible. The principle is the same: OpenClaw orchestrates locally, Jentic executes externally.
Architecture Diagram
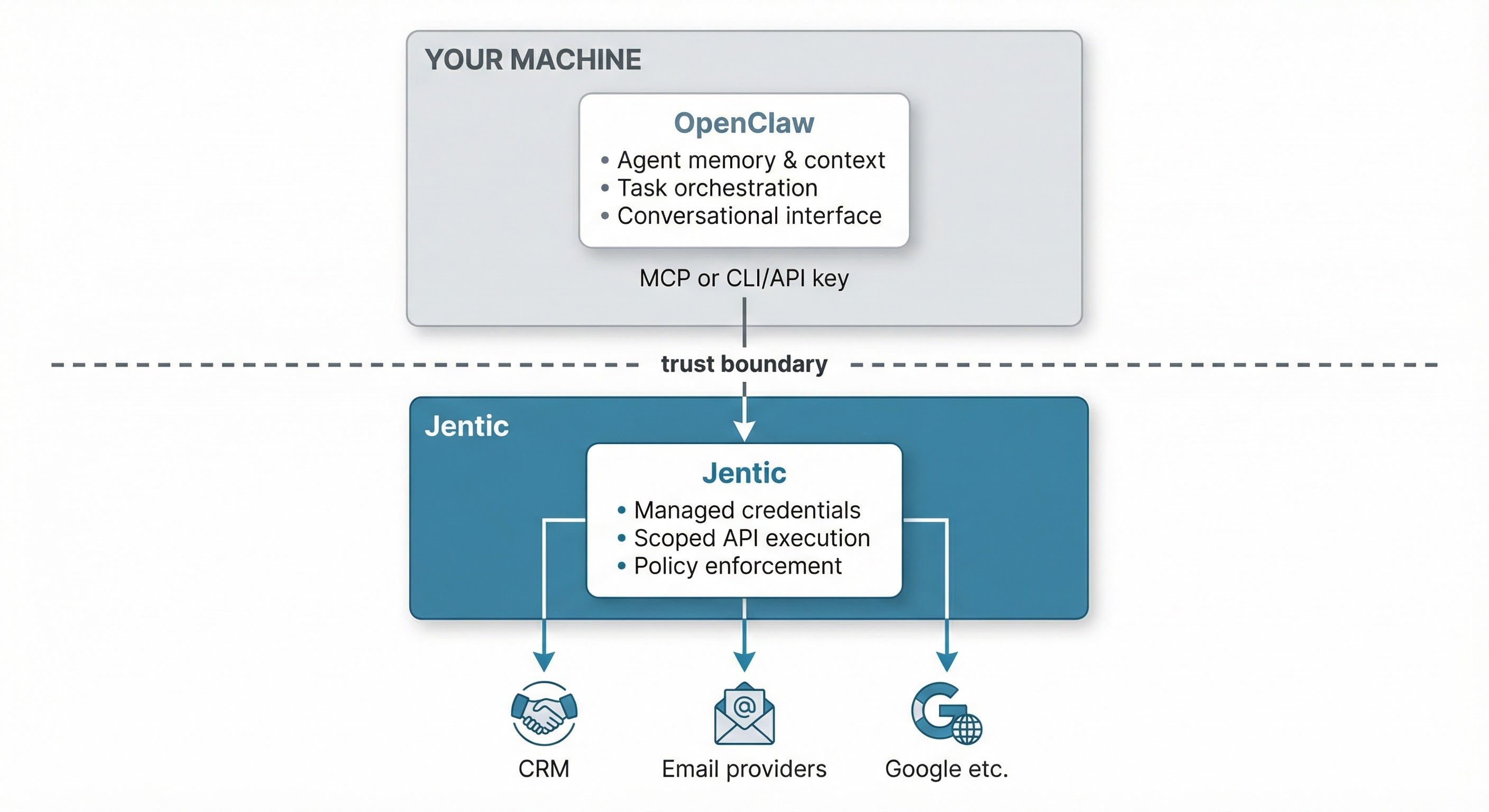
The trust boundary in the middle is the whole point. If the OpenClaw instance is compromised, the attacker gets the orchestration layer but not the keys to external services. Credentials never appear in config files, prompts, or client code. The skeleton key problem goes away.
Why This Pattern Matters Beyond PayKali
We're seeing this same architecture question come up across the OpenClaw community. The specifics vary but the core tension is always the same: people want powerful, autonomous agents that can reach into external systems, but they don't want a single compromise to hand over access to everything.
Jentic solves this at a few levels:
Credential Leakage
The most obvious one. When credentials are managed by Jentic, they never sit on your local machine. The agent requests access to a capability, Jentic handles auth server-side.
Skill Supply Chain Risk
When your external integrations come from a curated catalog of over 1,500 APIs described in open standards backed by the Linux Foundation, you're not downloading and running arbitrary code packages on your local machine.
Prompt Injection Scope
When tool execution is isolated, a compromised prompt can trick the agent into requesting an action, but the execution layer can enforce policies and validate parameters independently of whatever the LLM thinks it should be doing.
Blast Radius
The one that matters most. Even in a worst case where an OpenClaw instance is fully compromised, customer data in your CRM, credentials for third-party services, access to Google Workspace... all of that remains behind Jentic's execution boundary.
Getting Set Up
If you're running OpenClaw today and this resonated, here's how to get started. It takes minutes, not days.
-
Go to app.jentic.com and create a free account.
-
From the web app, create your API registry. This is your collection of integrations: pick from public APIs in the Jentic API directory and upload any private APIs your team uses.
-
Create credentials for each API in your registry.
-
Once your credentials are set up, you have two options:
- Create an MCP configuration to get a secure MCP endpoint, or
- Generate an API key for direct CLI access
Either way, you can expose Jentic to OpenClaw, Claude, Co-Work, ChatGPT, Cursor, whatever you're building with. Your agent gets access to the integrations it needs, and the credentials never leave Jentic's managed environment.
Full setup docs are at docs.jentic.com/guides/openclaw.
Conclusion
The OpenClaw ecosystem is going to keep growing. The agents are going to keep getting more capable. McCann and the PayKali team decided early to solve the security boundary at the architecture level rather than bolting it on later. That's the kind of decision that looks obvious in hindsight but takes real foresight to make in the middle of building something fast.
If you're building on OpenClaw and moving fast, take an hour to look at where your credentials actually live. Then come talk to us.
Jentic is the standardized tooling and security layer for AI agents. Managed authentication, 1,500+ integrations, built on open standards. Learn more